IDS Rules Editor Interface¶
The IDS Rules Editor Interface will enable you to edit & tune individual IDS Rules, including the IDS Rule Source code, status, Categories.
Moreover it lets you override some of the rule settings without the need to change the source code, We will explain various features by explaining each section in the image below
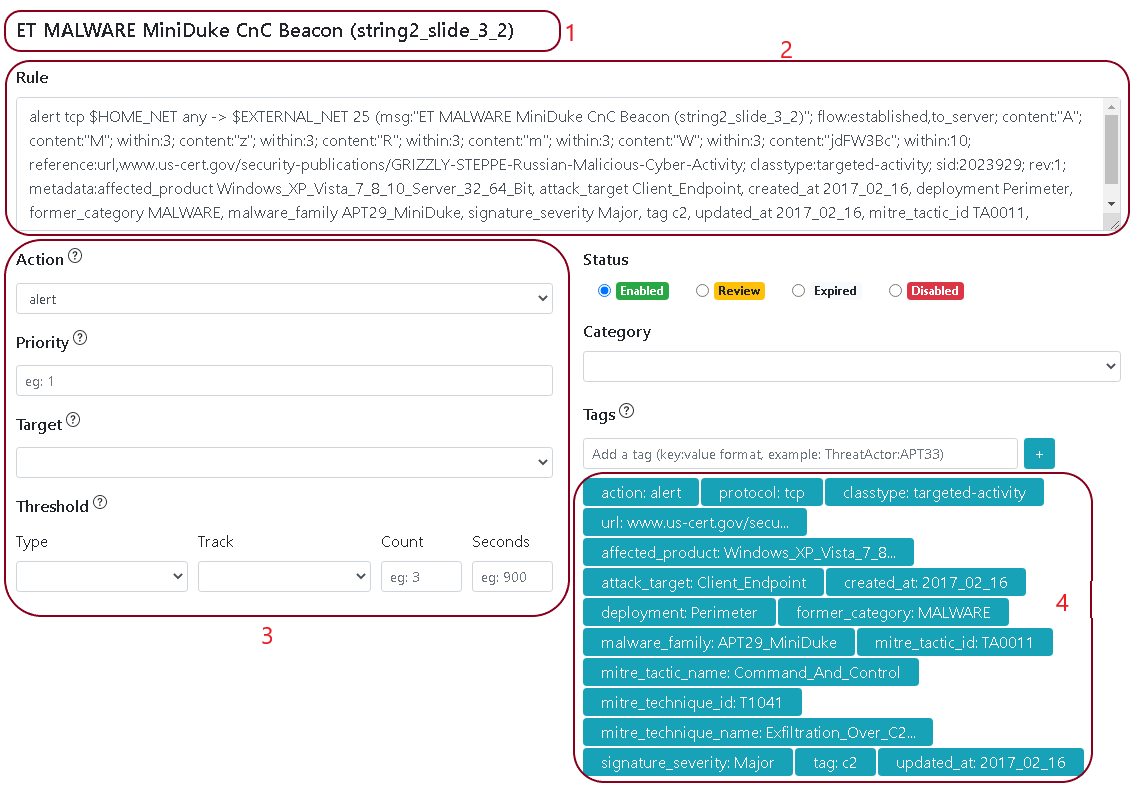
1. IDS Rule Alert Message.
2. IDS Rule source code.
3. The Rule option that you can override without having to edit the source code.
IDSTower allows you to set some of the rule tunning option without having to update the source code, this is important since updating the source code of the rule will introduce several issues, including:
the process is time consuming and error prone, since you will need to verify that the Rule is syntactically correct and is accepted by the IDS.
you will need to merge any changes/updates when a new revisions are published.
for this IDSTower enables you to set those tunning options from the interface and they will be intelligently inserted to the rules when try are sent to the IDS Hosts, they will also override the values of those options if they already exist in the rule source code.
Moreover, those tunning will be copied to any newly imported rule revisions so that you don’t have to manually set them again.
Example: you can set Threshold settings from interface to reduce the amount of alerts generated by a noisy rule, IDSTower will insert/override the threashold setting in the final rule source code sent to the IDS Hosts.
4. The IDS Rule Tags.
IDSTower extract various tags from rules, those tags includes references, url, hashes, CVEs…etc, it allows you as well to add tags, those added tags serves several purposes.
they allows you to “tag” and group rules bases on any key value pairs you choose, eg: you can Add a tag named ThreatActor with Value APT29 to all rules targeting this threat actor, this helps you maintain & group you detection logic better.
those tags adds more context to your analyst/engineer when they are triaging alerts, it would be super useful to know the vulnerability CVE number or malware hash value when investigating an alert.
those tags will be as well inserted to the final rule source code sent to the IDS hosts, specifically in the rule metadata keyword, this will means the generated alert will contain those tags, which will add more context to the generated alerts as well.