Generic json feeds¶
Many of the threat intelligence feeds publishes their IOCs as Json files, IDSTower support importing these feeds.
To add a Json feed to IDSTower, please follow the below steps:
Navigate to Settings->Feeds Tab->Add New Feed.
Set the Feed Name and Feed url.
Under type select “Indicators of Compromise (IOCs)”.
Under Feed Format option, select “JSON”.
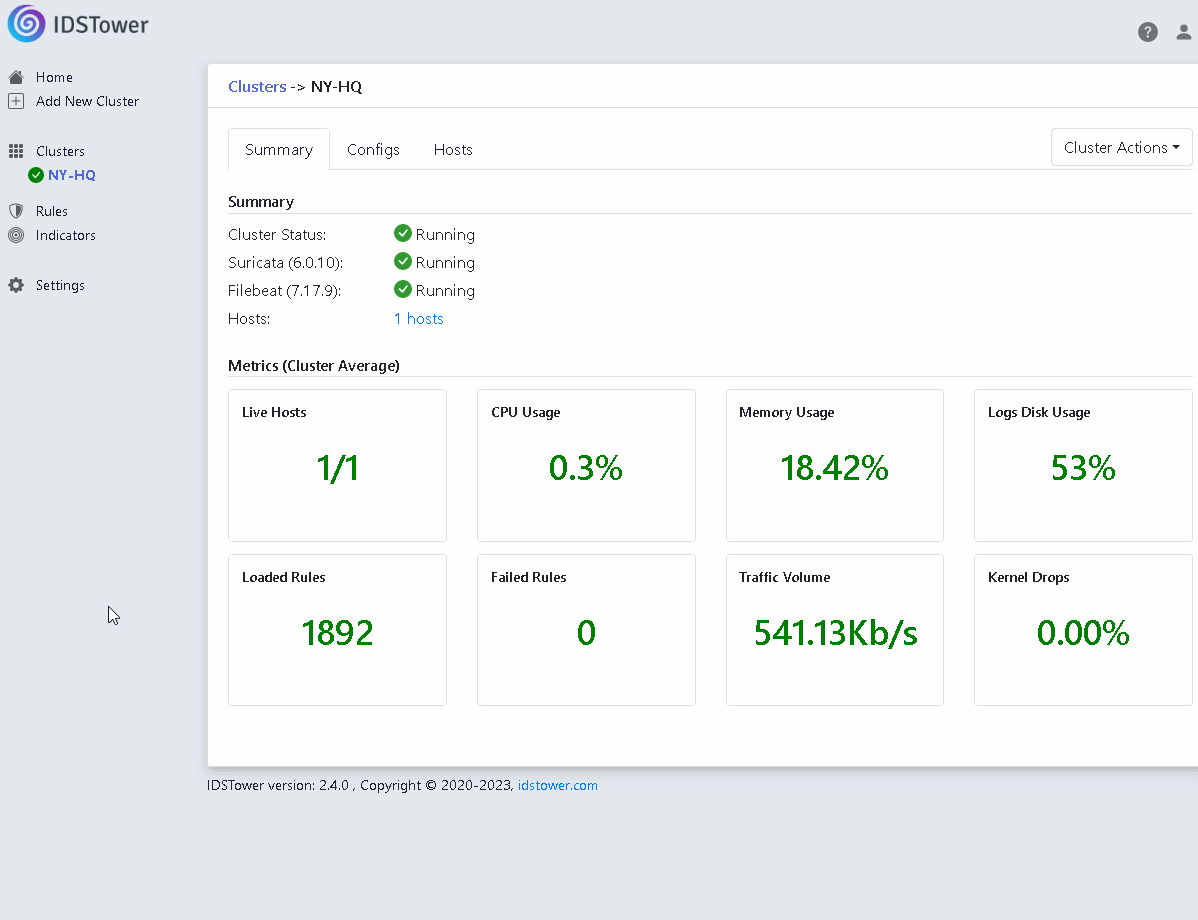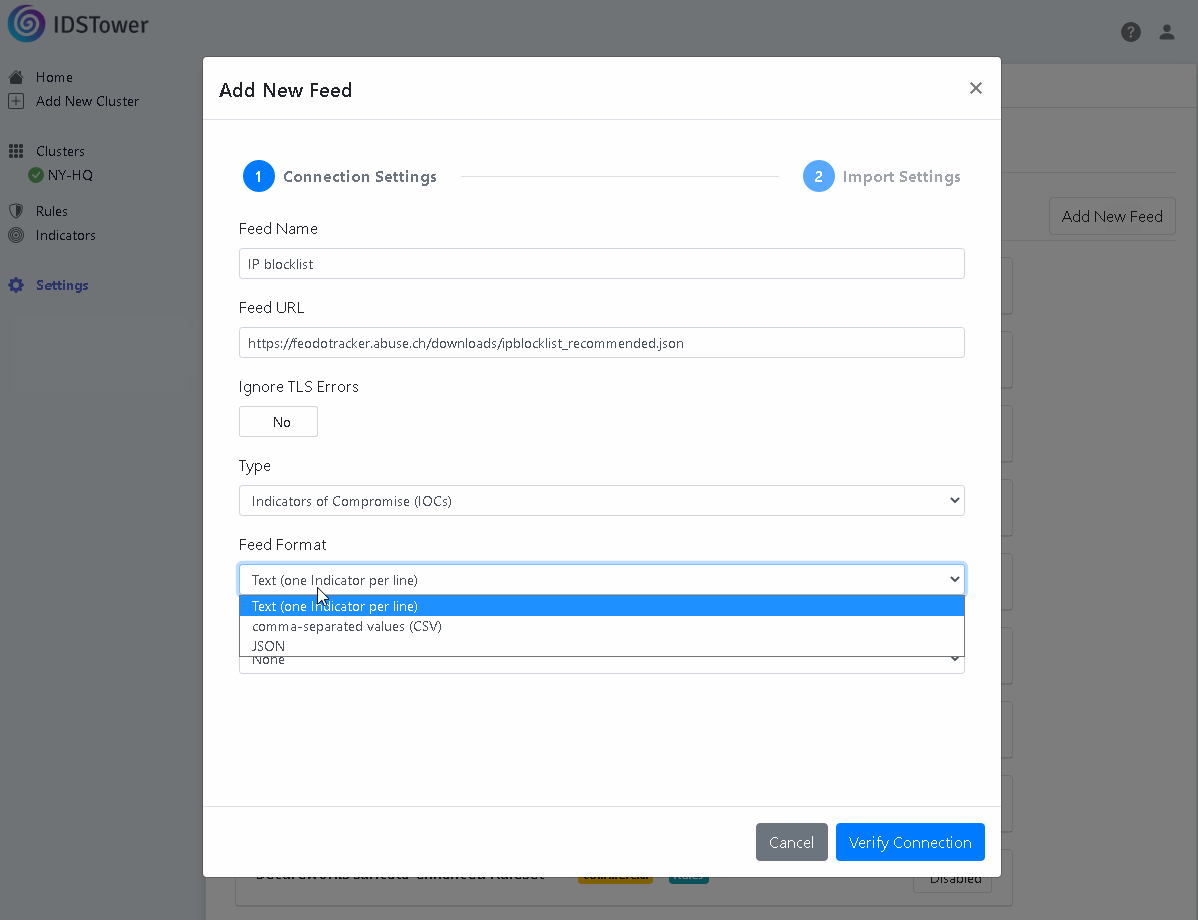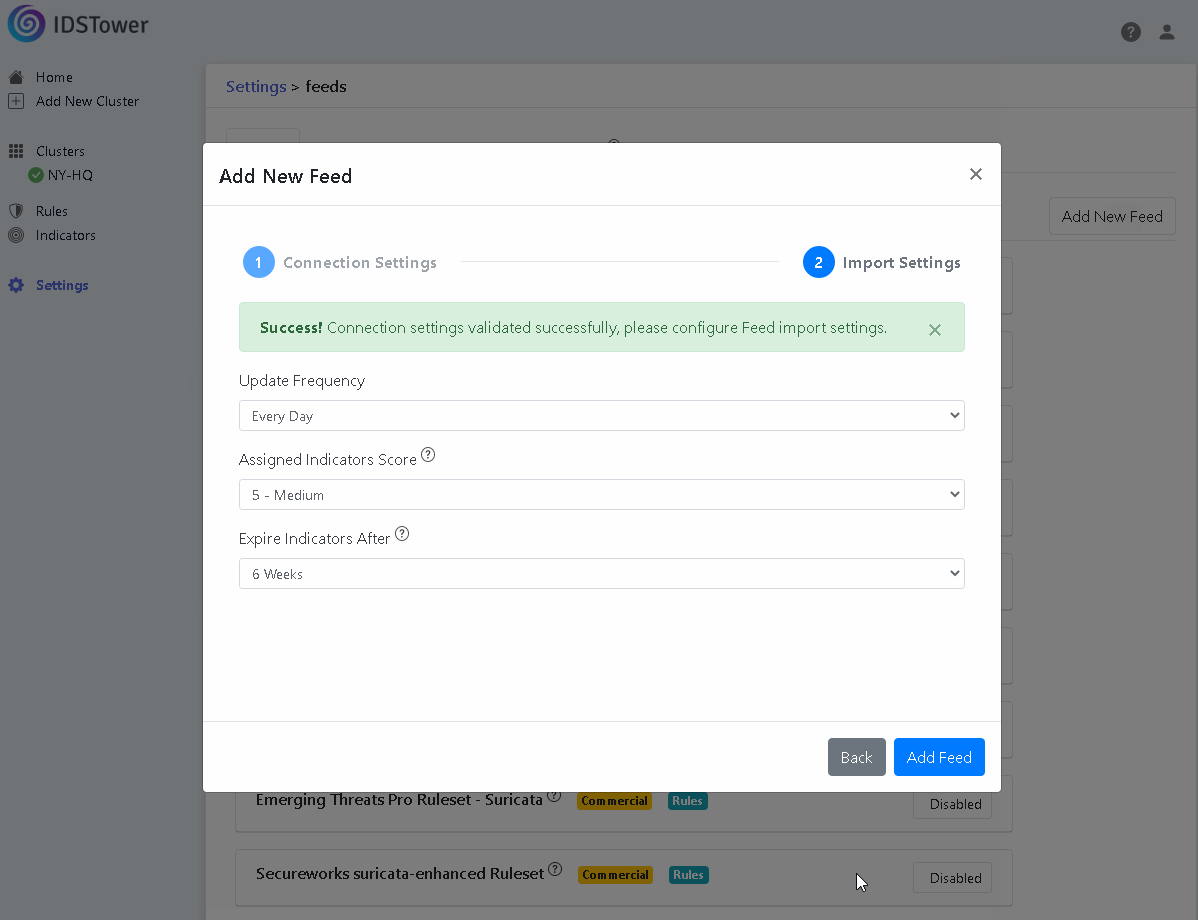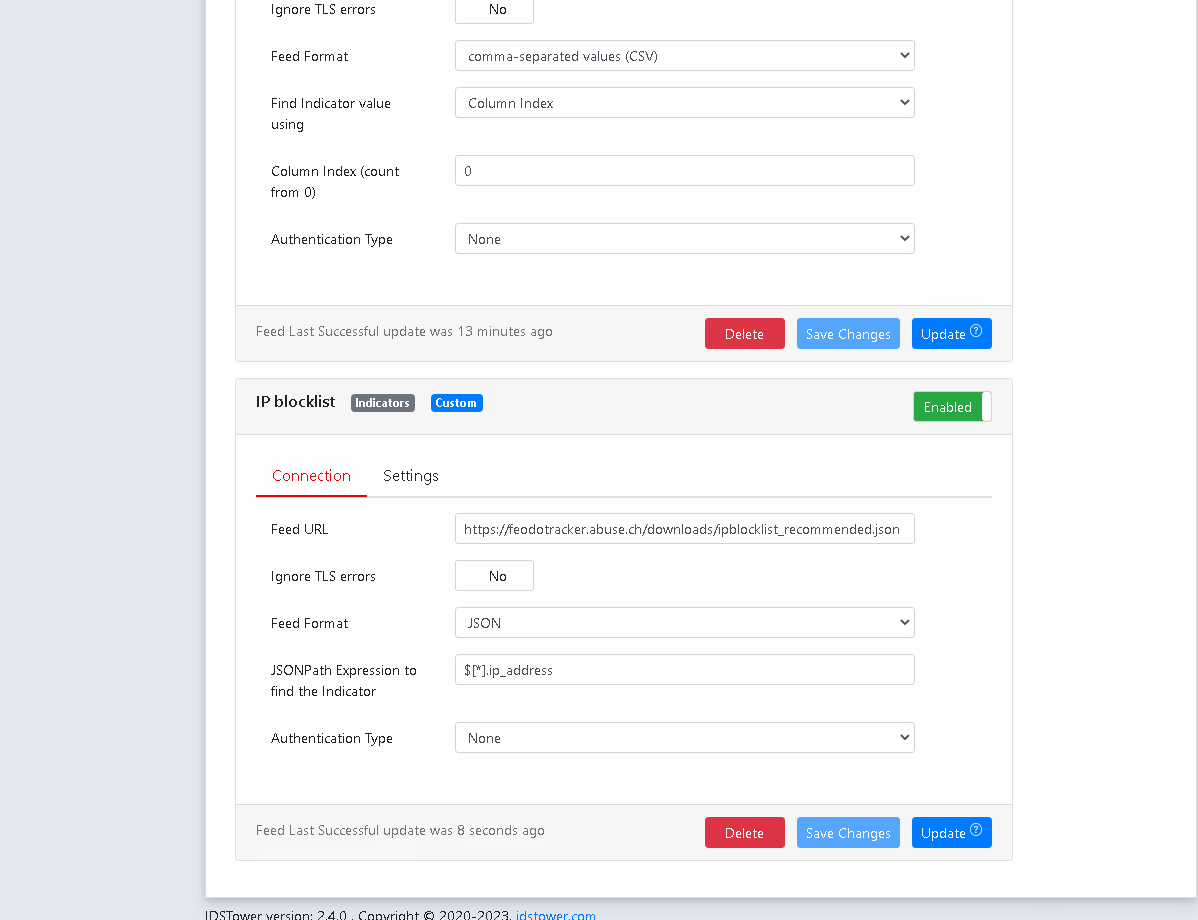
Enter the JSONPath Expression that IDSTower should use to locate the indicator value in the Json file, you can use online JSONPath evaluators to test the JSONPath Expression before using it in IDSTower.
Tip
JSONPath is a query language for JSON, similar to XPath for XML. It allows you to select and extract data from a JSON document.
Under authentication, select the appropriate authentication that the feed uses.
Click on “Verify Connection”, in this step IDSTower will verify that both the URL and the authentication credentials provided are valid.
Update the feed import settings if needed, then click on “Add Feed”.
The feed is now added and the IOCs will be imported periodically to IDSTower and send to Suricata hosts, you can trigger the feed download immediately by clicking on “Update” on the feed section.
In the following video, you can see the steps to add an abuse.ch Feodo tracker recommended IP Block list json feed to IDSTower: