Configuring IDS Rules & IOCs Export to AWS Network Firewall¶
In this guide we will configure IDSTower AWS Connector to export our IDS Rules & IOCs to AWS Network Firewall.
Adding the Export¶
In the AWS Connector tab, click on “Add AWS Export”.
Starting filling export settings, first choose a name for the export.
Choose the export credentials
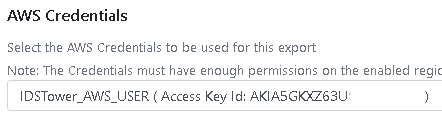
Select AWS regions to export Rules & IOCs to, you can select multiple regions.
Note
When you select multiple AWS regions, IDSTower will export the same copy of Rules & IOCs to every AWS region that was selected.
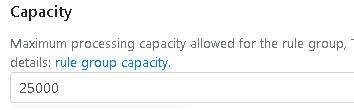
Set the export capacity, this will set the stateful rule group capacity.
Note
AWS Network Firewall won’t let you alter the capacity of a stateful rule group once created, IDSTower Connector tries to overcome this by attempting to delete and recreate the rule group (with the new capacity setting) if the capacity settings has been changed, this requires however, that the rule group is not associated with any firewall policy at that time.
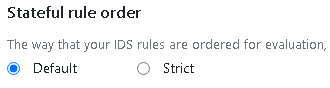
(Optional) The Stateful rule order settings controls how you rules are evaluated, keep this setting unchanged if unsure, for more details: Evaluation order for stateful rule groups
Choose what you wish to export to AWS.
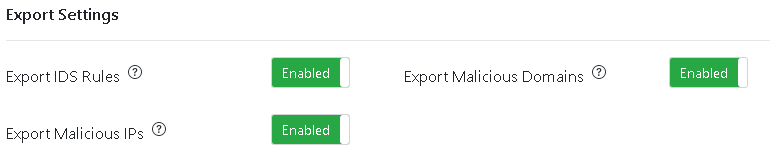
This screen allows you to configure rules import behavior:
Export IDS Rules: When Enabled, IDSTower Connector will export enabled IDS Rules from IDSTower to the configured regions as a stateful rule group that has the configured capacity & stateful rule evaluation order, the exported group will have the name: IDSTower-suricata-rules
Export Malicious Domains: When Enabled, IDSTower Connector will export enabled FQDN IOCs from IDSTower to the configured regions as a stateful rule group that has the configured capacity & stateful rule evaluation order, the exported group will have the name: IDSTower-malicious-fqdns
Export Malicious IPs: When Enabled, IDSTower Connector will export enabled IP & IP_PORT IOCs from IDSTower to the configured regions as a stateful rule group that has the configured capacity & stateful rule evaluation order, the exported group will have the name: IDSTower-malicious-ips
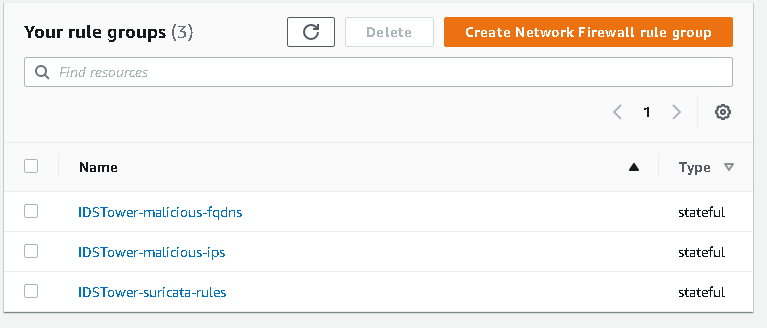
Below is an example of how the exported AWS Network Firewall rule groups will lock like in your AWS Console:
(Optional) set the IDS Rules variables, details: Suricata Rule-vars
Note
Make sure to click on the “Add” button after entering the rule variable details so that the variable gets created.
Finally, Click “Verify & Add”, once clicked, IDSTower will verify that the provided credentials have the required permissions (eg: create, update & delete), if all is good, the export will be added as below:

Tip
When you attempt to add the export, IDSTower will verify that the selected credentials have the required permissions to create and update the stateful rule groups in the selected AWS Regions.
In the previous steps, we have created & configured our first export, this will tell IDSTower connector what/where/how to export both the IDS Rules and IOCs, however nothing has been exported yet.
Next, we will run the export manually to verify that everything is working fine.